Cyber Security Analyst Course
 A cybersecurity analyst safeguards an organization's networks, hardware, and software from cyberattacks while also ensuring the security of the organization's information systems.
A cybersecurity analyst safeguards an organization's networks, hardware, and software from cyberattacks while also ensuring the security of the organization's information systems. An information security analyst would also think about the security of data housed elsewhere, such as records in an archive or insider information held by some employees.
An information security analyst would also think about the security of data housed elsewhere, such as records in an archive or insider information held by some employees. The SevenMentor Cyber Security Analyst Course has classes that explain cyber attacks, malware, and hackers' behaviours.
The SevenMentor Cyber Security Analyst Course has classes that explain cyber attacks, malware, and hackers' behaviours.
CONSULT WITH
OUR ADVISORS
- Course & Curriculum Details
- Flexible Learning Options
- Affordable Learning
- Enrollment Process
- Career Guidance
- Internship Opportunities
- General Communication
- Certification Benefits
Request Call Back
Learning Curve for Cyber Security Analyst
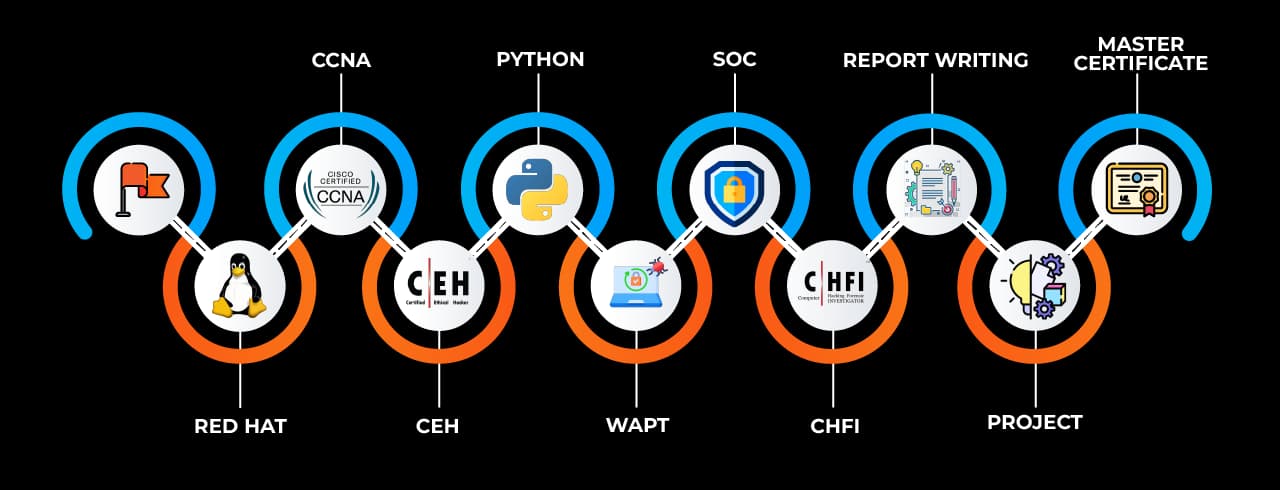
Why Choose SevenMentor Cyber Security Analyst
Empowering Careers with Industry-Ready Skills.
Specialized Pocket Friendly Programs as per your requirements
Live Projects With Hands-on Experience
Corporate Soft-skills & Personality Building Sessions
Digital Online, Classroom, Hybrid Batches
Interview Calls Assistance & Mock Sessions
1:1 Mentorship when required
Industry Experienced Trainers
Class Recordings for Missed Classes
1 Year FREE Repeat Option
Bonus Resources
Specialized Pocket Friendly Programs as per your requirements
Live Projects With Hands-on Experience
Corporate Soft-skills & Personality Building Sessions
Digital Online, Classroom, Hybrid Batches
Interview Calls Assistance & Mock Sessions
1:1 Mentorship when required
Industry Experienced Trainers
Class Recordings for Missed Classes
1 Year FREE Repeat Option
Bonus Resources
Fastest 1:1 doubt support
Flexible EMI Plans
Adaptive LMS
Free Wifi Facilities
Flexible Scheduling
Ongoing Career Support
Placement Drives
GitHub Project Implementations
Real World Topics
5/5 rating for 99% doubt Solutions
Be Different With Master Certificate
Latest Market Technology & Practical Training
Resume Building Session & Job Portals Training
Enhanced Capstone Projects for learning
Stand Out with an impressive Certificate
Weekday and Weekend Batches
Workshops & Seminars with Industry Experts
Unlimited Interview Calls
AWS Cloud Project Deployments
Live Quizzes
Resolve doubts any time through chat, voice notes, calling or meeting with instructors.
Curriculum For Cyber Security Analyst
BATCH SCHEDULE
Cyber Security Analyst Course
Find Your Perfect Training Session
Feb 15 - Feb 21
2 sessionsFeb 22 - Feb 28
1 sessionsMar 1 - Mar 7
1 sessionsLearning Comes Alive Through Hands-On PROJECTS!
Comprehensive Training Programs Designed to Elevate Your Career
No active project selected.
Transform Your Future with Elite Certification
Add Our Training Certificate In Your LinkedIn Profile
Our industry-relevant certification equips you with essential skills required to succeed in a highly dynamic job market.
Join us and be part of over 50,000 successful certified graduates.

Course Content
Frequently Asked Questions
Everything you need to know about our revolutionary job platform
Who is qualified for the cyber security course?
What qualifications do cyber security analysts have?
Is being a cybersecurity analyst a viable career option?
Is cybersecurity a high-paying field?
Do you think cybersecurity has a future?
Will artificial intelligence (AI) take over cybersecurity?
What exactly are the 5 C's of Cybersecurity - Innovative Networks?
What exactly is the objective of cyber security?
What is the role of cyber security?
What constitutes the four rules governing cyber security?
Is it premature to switch to safety if you're in your thirties or older?
What is the typical job path for a cyber security analyst?
Is there a strong demand for cybersecurity professionals? Demand is high.
Will artificial intelligence (AI) replace cybersecurity workers?
What elements distinguish cyber security?
Explore Other Demanding Courses
No demanding courses available at the moment.
Debug: courses prop type: object, isArray: yes, length: 0




