DHCP PROTOCOL
The Dynamic Host Configuration Protocol (DHCP) is a network protocol that allows a server to automatically assign an IP address to a device when it connects to the network. The DHCP process consists of four main steps: DHCP discovery, DHCP offer, DHCP request, and DHCP acknowledgment.
- DHCP Discover: When a device connects to a network, it sends a broadcast message known as a DHCP discover message. This message is sent on the local subnet and contains the device’s MAC address and a request for an IP address.
- DHCP Offer: The DHCP server, which is responsible for managing IP addresses on the network, receives the DHCP discover the message and sends a DHCP offer message in response. This message contains an available IP address, along with the subnet mask, default gateway, and DNS server information.
- DHCP Request: The device receiving the DHCP offer message sends a DHCP request message, indicating that it would like to accept the offered IP address.
- DHCP Acknowledgement: The DHCP server sends a DHCP acknowledgment message, which confirms that the IP address has been assigned to the device and provides the lease time for the IP address.
For Free, Demo classes Call: 020-71173071
Registration Link: Click Here!
Once the DHCP process is complete, the device has been assigned an IP address and other network configuration information and can communicate on the network. The DHCP lease time determines how long the IP address is valid, and when the lease expires, the device must request a new IP address through the DHCP process. SevenMentor is the best institute for CCNA Training in Pune. Practical learning with 100% placement assistance.
In addition to IP address assignment, DHCP also supports other options such as DHCP relay, DHCP option 82, DHCP snooping, etc. DHCP relay is used to forward DHCP messages between different network segments, DHCP option 82 is used to identify the device and location from which the DHCP request originated, and DHCP snooping is used to filter untrusted DHCP messages and ensure DHCP integrity.
Overall, DHCP is a powerful tool for simplifying network management and ensuring that each device on the network has a unique IP address. It is widely used in enterprise and home networks to automate IP address allocation and reduce administrative overhead.
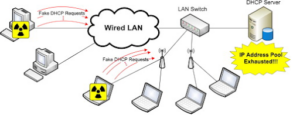
DHCP SPOOFING ATTACK
DHCP spoofing, also known as DHCP starvation or DHCP exhaustion attack, is a type of attack where a malicious device on the network poses as a DHCP server and assigns itself a high IP address, becoming the default gateway for all other devices on the network.
During the attack, the attacker sends out a large number of DHCP discover messages, overwhelming the legitimate DHCP server and causing it to run out of available IP addresses. The attacker then sends a DHCP offer message with a fake IP address, which the victim device accepts as a valid IP address. As a result, the victim device establishes a connection with the attacker’s device, which then becomes the default gateway for the victim device.
For Free, Demo classes Call: 020-71173071
Registration Link: Click Here!
Once the attacker’s device is the default gateway, it can intercept and redirect network traffic. This allows the attacker to steal sensitive information or disrupt network communication. Additionally, the attacker can use this position to launch further attacks on other devices on the network or even on other networks.
There are different ways that DHCP spoofing attacks can be carried out, such as:
- DHCP Starvation: In this attack, the attacker floods the network with DHCP discover messages, causing the DHCP server to run out of IP addresses, and then sends a DHCP offer message with a fake IP address.
- DHCP Hijacking: In this attack, the attacker sends a DHCP offer message with a fake IP address that is higher than the IP addresses assigned by the legitimate DHCP server. As a result, the victim device accepts the fake IP address as a valid one.
- DHCP Rogue Server: In this attack, the attacker sets up a rogue DHCP server on the network, which assigns itself a high IP address and becomes the default gateway for all other devices on the network.
DHCP spoofing attacks can be mitigated by implementing DHCP snooping, which is a security feature that filters untrusted DHCP messages and only allows messages from trusted DHCP servers to pass through. Additionally, it builds and maintains a DHCP snooping binding table, which maps each device’s MAC address to its assigned IP address, to ensure that only valid DHCP packets are forwarded. Are you looking for Best CCNA Training? SevenMentor offers the best CCNA course in Pune
It’s also important to practice good network security hygiene such as, using strong passwords and limiting access to your DHCP server. Regularly monitoring your network and keeping your devices up-to-date with the latest security patches can also help to prevent DHCP spoofing attacks.
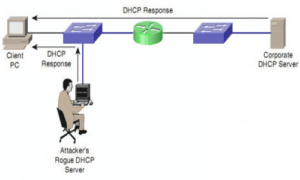
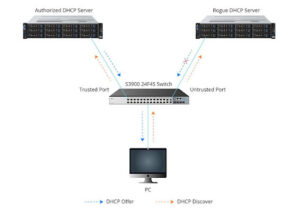
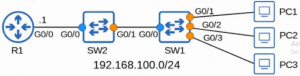
DHCP SNOOPING
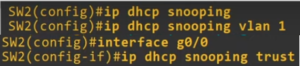
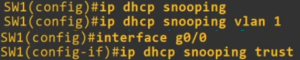
DHCP snooping is a security feature that helps to prevent malicious DHCP server attacks on a network by filtering untrusted DHCP messages. It acts as a filter for DHCP messages, only allowing messages from trusted DHCP servers to pass through. It also builds and maintains a DHCP snooping binding table, which maps each device’s MAC address to its assigned IP address, to ensure that only valid DHCP packets are forwarded.
DHCP snooping can be configured on different network devices such as switches, routers, and firewalls. It works by creating a trusted and untrusted interface on the network device. The trusted interface is where the DHCP server is connected, and all DHCP messages received on this interface are considered to be legitimate. The untrusted interface is where the DHCP clients are connected, and all DHCP messages received on this interface are inspected to ensure their legitimacy. Seven Mentor is the best training provider in World with CCNA Classes in Pune
When a DHCP message is received on an untrusted interface, the DHCP snooping feature checks the DHCP snooping binding table to see if the MAC address of the device sending the message is mapped to a valid IP address. If the MAC address is not found in the table, the DHCP message is dropped. If the MAC address is found in the table, the DHCP message is forwarded.
Additionally, DHCP snooping can be used with DHCP option 82 and DHCP relay. DHCP option 82 is used to identify the device and location from which the DHCP request originated, and the DHCP relay is used to forward DHCP messages between different network segments.
For Free, Demo classes Call: 020-71173071
Registration Link: Click Here!
In summary, DHCP snooping is a security feature that can be implemented on network devices to protect against DHCP spoofing attacks. It filters untrusted DHCP messages, only allowing messages from trusted DHCP servers to pass through, and maintains a DHCP snooping binding table that maps each device’s MAC address to its assigned IP address. It also can be used in conjunction with DHCP option 82 and DHCP relay to ensure the integrity of the DHCP process and enhance the security of the network.
![]()
Author:
Khatib Samir
Call the Trainer and Book your free demo Class for CCNA now!!!
© Copyright 2021 | SevenMentor Pvt Ltd.

